Cybersecurity: 2020
Threat actors have a very real opportunity to make big returns.
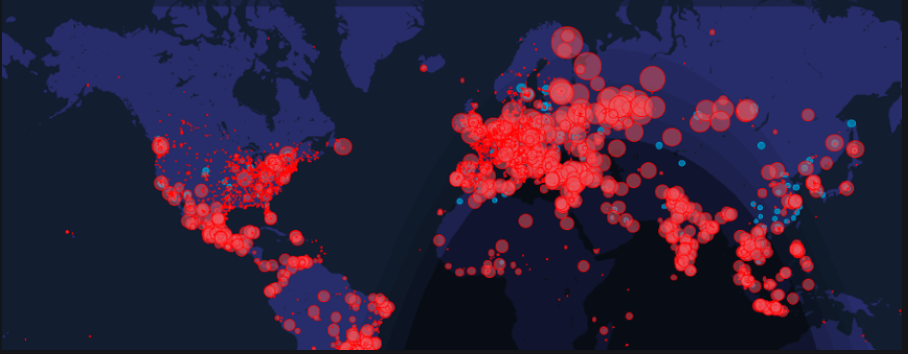
In the cybersecurity world, the bad guys are picking up the pace and the deluge of attacks isn’t likely to let up. Experts predict bolder actions and attacks by threat actors, and stricter regulations and lawsuits by regulators and consumers. Cybercrime will intensify in 2020 and could cost a lot.
Collaboration across criminal groups with differing specialities is one of the most significant developments in criminal techniques that will shape cybercrime in 2020. Hackers are now selling access to networks they previously compromised to other threat groups. This type of collaboration among threat actors allows one group of criminals to leverage the work of another group of criminals. By purchasing access to a target’s breached network, a cybercriminal can distribute ransomware without having to do any initial breaching on their own.
Cyber-criminals also refined attack techniques that will become more the norm in 2020. Bad actors began to commonly use precursor infections to find high-value systems and encrypt data on them, making victims more likely to pay. Targets themselves are no longer mass-scale victims of spam, but instead are specifically selected. Many criminals know with whom they are dealing and act accordingly.

“Malware threat actors are increasingly trading their work…”
Sophisticated tools developed in 2019 also give a foretaste of what is to come in 2020. Ransomware that uses “kill lists” to try and terminate anti-malware tools, or malware that sets itself up as a service running in Windows’ Safe mode avoids all built-in protection tools and increases the criminals chance of success. Malware can now be automated to quickly profile an infected environment and laterally spread within a targeted network, or trigger simultaneous infections across multiple machines within the same environment.
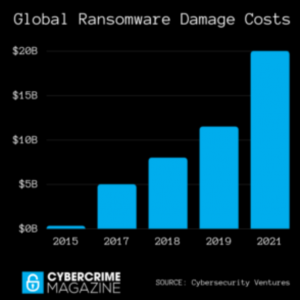
Government regulations are expected to become more strict as vulnerabilities to cyberattacks increase. In 2019 Juniper Research predicted that annual costs of data breaches will rise 11% per year to over $5 trillion in 2024, driven mainly by higher fines as well as business losses incurred due to a cybersecurity incident.

“Most fines and lost business are not directly related to breach sizes.”
Late in 2019, a proposed class-action lawsuit against a medical services company LifeLabs sought more than $1.13 billion in compensation for LifeLabs’ clients after a database hack compromised personal and health information of up to 15 million customers. While this large-scale suit will grind through the slow legal process, the verdict in the court of public opinion is in. Customers in 2020 will presume their data is protected and will expect companies of all sizes to be punished for failing to protect it.
In 2020 cybersecurity will only become more important for companies doing business in a digital world. Near-constant breaches in 2019 have created a numbness to security risks, while the complexity of technology and sophistication of cyber threats makes IT security feel daunting to businesses. Partner with Ostra in 2020 for an Enterprise Grade Security solution that combines top tier appliances and services for strong cybersecurity protection.
As Your Trusted Cybersecurity Team, Ostra makes cybersecurity simple and accessible to businesses of all sizes. Ostra provides its partners and their clients with a multi-layered, comprehensive and fully managed Security as a Service.




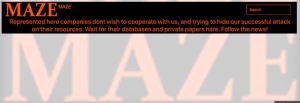






 The ransom note indicated this was a targeted attack against CyrusOne’s network. Targeted attacks rely on single-use strains of malware specifically designed to avoid detection by signature-based antivirus solutions. Successful defense against this type of attack requires integrated prevention, detection and response tools that recognize and halt advanced threats.
The ransom note indicated this was a targeted attack against CyrusOne’s network. Targeted attacks rely on single-use strains of malware specifically designed to avoid detection by signature-based antivirus solutions. Successful defense against this type of attack requires integrated prevention, detection and response tools that recognize and halt advanced threats. 